Warning to Android Crypto Users: New ‘Pixnapping’ Attack Can Steal Seed Phrases Directly From Your Screen
Cybersecurity researchers at Carnegie Mellon University have identified a new Android vulnerability that could allow hackers to steal sensitive on-screen data, including crypto wallet seed phrases and two-factor authentication (2FA) codes, without special permissions.
The attack, named Pixnapping, targets devices from Google and Samsung and uses a previously known GPU side-channel technique called GPU.zip.
The attack begins when a user installs a malicious app, which then silently invokes another application, such as a crypto wallet or authentication app, from which it intends to extract data.
 Source: Pixnapping research paper
Source: Pixnapping research paper
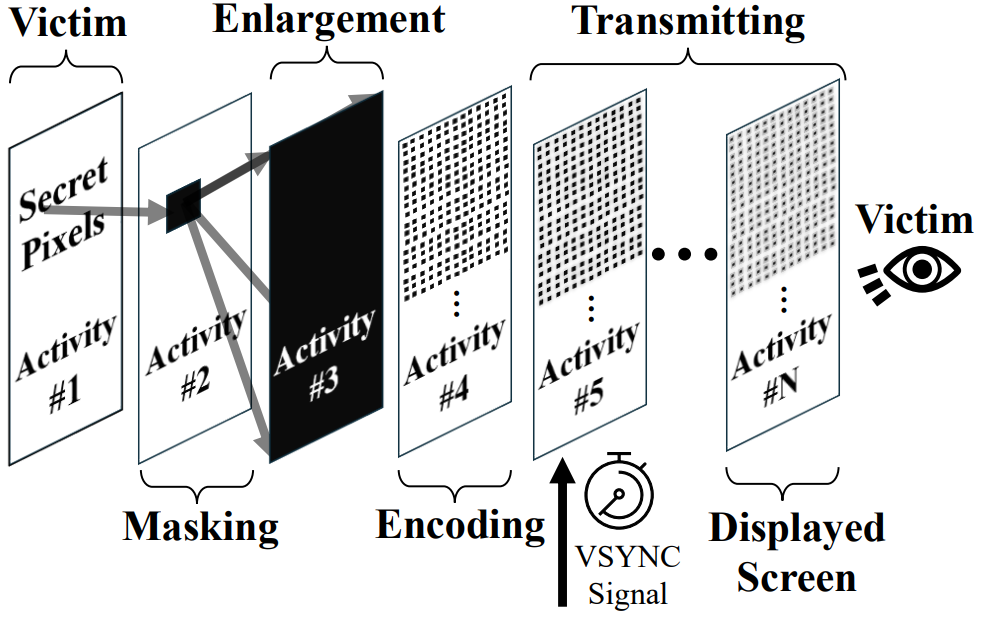
It manipulates graphical operations on specific pixels where sensitive information is typically displayed, reconstructing those pixels one by one through side-channel timing analysis.
Researchers compared this process to taking unauthorized screenshots of data visible on the screen.
Pixnapping uses Android’s window blur API and VSync callbacks to force sensitive pixels into the rendering pipeline, layering semi-transparent activities to measure how long certain frames take to render.
These timing patterns reveal the color value of each pixel, which can then be reconstructed to expose sensitive data.
Pixnapping Exploit Targets Screen Pixels to Bypass Android App Isolation
The attack has been successfully demonstrated on the Google Pixel 6 through Pixel 9 devices, as well as the Samsung Galaxy S25, running Android versions 13 through 16.
Tests showed that the researchers were able to recover 2FA codes from Google Authenticator with success rates between 29% and 73%, depending on the device model.
On average, the attack retrieved a full six-digit code in under 30 seconds, fast enough to exploit the brief validity period of most 2FA codes.
The team noted that while recovering long recovery phrases would take more time, crypto seed phrases remain highly vulnerable if left visible while being written down.
Since these phrases stay on the screen longer than time-sensitive codes, attackers could potentially reconstruct them pixel by pixel if users are not cautious.
The vulnerability, tracked as CVE-2025-48561, was reported to Google in February 2025. A partial patch was issued with September’s Android security update, but the researchers said they found a workaround that allows the attack to continue functioning.
Google has since acknowledged the issue as high severity and confirmed that a second fix is being developed, expected in December.
In their tests, the researchers were able to extract sensitive data not only from crypto wallets and Google Authenticator but also from applications like Gmail, Signal, Venmo, and Google Maps.
Because the exploit targets visible screen content rather than stored files or permissions, even strict app isolation measures fail to block it.
According to the researchers, Google initially attempted to mitigate the flaw by limiting how many activities an app can blur simultaneously, but this proved insufficient. They have also alerted Samsung that the patch does not protect its devices.
Security experts advise crypto users to avoid displaying recovery phrases or 2FA codes on internet-connected devices.
Instead, they recommend using hardware wallets, which store private keys and recovery phrases offline, preventing exposure through screen-based attacks like Pixnapping.
Crypto Investors Face Rising Android Malware Threats
A surge in Android-based crypto malware has intensified global cybersecurity concerns, with several major incidents surfacing over recent months.
In April, researchers uncovered “Crocodilus,” a remote-access trojan targeting crypto wallet users in Turkey and Spain. Exposed by ThreatFabric, the malware disguises itself as legitimate crypto apps, tricking victims into revealing their seed phrases through fake security alerts.
Once installed, it abuses Android’s Accessibility Services to steal passwords, intercept two-factor codes, and capture wallet credentials, all while masking activity behind a black-screen overlay.
Security experts say Crocodilus spreads through multiple channels, including phishing emails, compromised websites, and malicious ads, making it difficult to trace the original dropper.
The discovery follows reports of broader malware campaigns tied to fake AI, gaming, and Web3 startups.
According to cybersecurity firm Darktrace, attackers have built convincing online presences, complete with fake company websites, social profiles, and GitHub repositories, to lure users into downloading infected software.
The campaigns use malware families such as Realst and Atomic Stealer, capable of exfiltrating wallet data on both Windows and macOS.
Analysts warn that these scams represent a growing sophistication in crypto-focused attacks, combining social engineering with advanced obfuscation and persistent execution methods.
Cybersecurity experts advise users to verify project legitimacy, avoid downloading software from unverified sources, and remain cautious of unsolicited offers or airdrops, especially those linked to new “startups” or crypto platforms promising exclusive access or rewards.
You May Also Like

MoneyGram launches stablecoin-powered app in Colombia

Pluvo Raises $5M Seed Round to Build the AI Decision Intelligence Platform for Modern Finance Teams
